You might have heard of DNS hijacking lately, or you might have come across DNSpionage in the news. Warnings were issued by the Cybersecurity and Infrastructure Security Agency of the US Department of Homeland Security, by the UK National Cyber Security Centre and by other leading security enterprises, like Cisco, Talos, FireEye, and Akamai that ongoing DNS hijacking attacks threaten public authorities, enterprises and all kinds of businesses in multiple countries around the world, including the USA, Germany, and Sweden.
It's clearly time to act. But how can DNS hijacking threaten email?
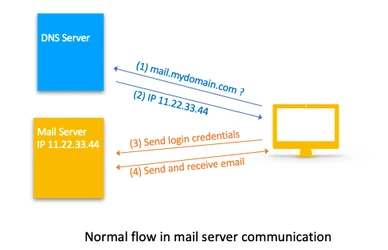
DNS is short for Domain Name Service. The internet infrastructure uses IP addresses that are hard to memorize for humans. Therefore, we use domain names which are symbolic names that need to be translated to the technical IP address. That's what the DNS is for. If you enter a domain name in your browser's address bar, your computer will send a query to a DNS server to ask for the server IP address that is behind that domain name and that is needed to connect to that server.
However, if that DNS server returns the wrong IP address, the client connects to that address without knowing that it's not really the server behind the domain name.
This cannot only happen with web servers, but also with mail servers. If your mail client connects to your mail server, it will send your personal credentials to the server to authenticate and exchange your personal email with it. But if it's not the correct server but a fake server, all clients connecting to that server will inadvertently reveal the users login data to the fake server!
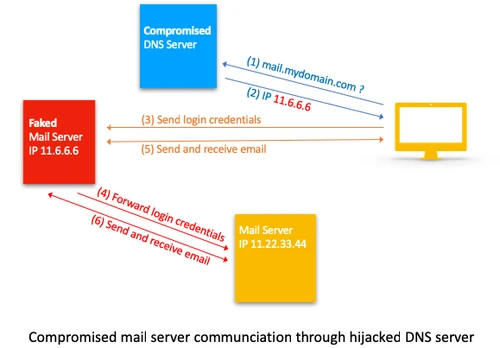
Not only will this expose all emails currently stored on the server, it also enables the attacker to continue to spy out your email until the password is eventually changed.
Note that the attacker does not need to hijack the DNS for long. It has been reported that the DNS was hijacked for not longer than an hour which is still enough time to collect many users' credentials, because most email clients are configured to check for new mail in short intervals.
The user will not notice a problem. It's not so unusual that a mail server does not deliver email for a short period that a user would become suspicious. But the fake mail server can even connect to the original server and pass through the email as if everything was in perfect order.
You may wonder how it is possible to hijack DNS servers in the first place. This, indeed, requires access to the DNS server. This can be accomplished through security holes or phishing attacks against the server administrators. It may not be too easy, but it's doable and worth the effort. Once control has been gained over the DNS server, it is possible to change the DNS response of virtually any domain.
Once the IP address has been exchanged by one that is under control of the attacker, the fake server behaves as if it was the original server. Even if the client requests an encrypted connection, the fake server can provide this as well.
Email encryption does not protect you from trusting a fake DNS server. There is method called DNSSEC that is said to help us with that. Yet, email encryption helps im another way.
If you used email encryption, even though your email is disclosed, the contents of your emails remains locked from the attacker. Remember that email encryption is genuine end-to-end encryption which means that just access to the email messages does enable the attacker to spy out their contents. Without the private keys required to decrypt the messages, even disclosed email remains protected.

Unfortunately, DNSpionage attacks are still ongoing. So, if you don't encrypt your email yet, take this as your call to action.